i3indya™ Technologies presents Practical Training on Ethical Hacking & Cyber Security.
If you want to know how hackers are attacking your websites, emails, servers & computer remotely or how you can protect yourself or your organization from all these attacks then this is the right course for you.
Ethical Hacking & Cyber Security (Summer Internship 2019)
30 Days / 45 Hrs (15 Days Training & 15 Days Internship Project Work)
Certificate of Completion by i3indya™ Technologies
E-Book & Softwares Free to each participant
20 Topics | Learn 100+ Secrets of Ethical Hacking
Noida | Gurugram | Hyderabad | Bangalore | Pune | Kolkata | Chennai
Click Here
Click Here
 Yes! You can Do This Course at Your Home by watching online video lecture's. See Details Here
Yes! You can Do This Course at Your Home by watching online video lecture's. See Details Here
| Module | Topics |
|---|---|
|
1 |
Need of Cyber Security Career opportunities in industry Virtualization Basic commands of Kali Linux |
|
2 |
IPv4 1Pv6 OSI Model Networking Devices Network Address Translation |
|
3 |
Enumeration & Information Gathering Information gathering WHOIS Traceroute Name server lookup |
|
4 |
Advanced information gathering Google dorks/Operators Spider/Crawler |
|
5 |
Ping & ping sweep Port scanning Vulnerability scanning |
|
6 |
Active attack Passive attack Default passwords |
|
7 |
Viruses Worms Trojans Rootkits Adwares Spywares |
|
8 |
Bypasing WEP Bypassing WPA/WPA2 |
|
9 |
HTTP vs HTTPS Automated SQL Injection XSS (CrossSite Scripting) |
|
10 |
DoS vs DDoS Countermeasures |
|
11 |
Introduction Types of encryption Hashing Stegnography |
|
12 |
IPS IDS Firewalls |
Latest and Updated Topics are covered
We concentrate not only on Hacking but also on Security of all Topics
Forensics on almost all platforms and devices are taught
Hands on training with live demonstrations
Well experienced Trainers
Tied up with several Government Organizations for Training and Consultancy
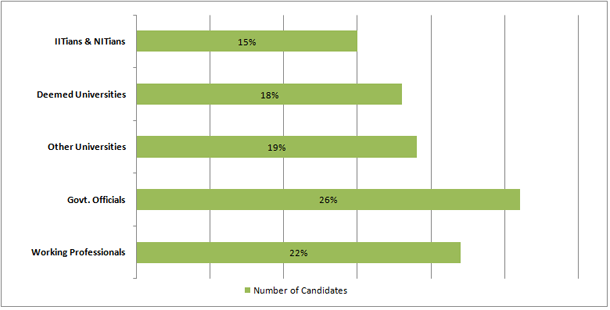
Trained more than 30,000 professionals from all over India
Providing training to CBI, NIA and State Police across India
We limit our tool usage from third-party and we provide manual approach for each Technique
We also design our own tools
Basics of Computer
Knowledge of how to use internet
Basics of Networking
 It is strongly recommended to bring your own LAPTOP during the training so that you can easily practice the exercises at home.
It is strongly recommended to bring your own LAPTOP during the training so that you can easily practice the exercises at home.
College students seeking career in Cyber Security Industry.
Person having interest in Hacking & Security.
Education Faculty & Staff.
IT Professionals, Web Developers, Network Engineers.
Students from any branch can join the training.